A few months back I put out a blog on what I was able to pull out of Bumble on iOS in terms of artifacts. Soon after I started working on the Android version as well but I totally abandoned work on it for months.
I recently took the Hexordia HEX-250 Mobile Analysis Methodology and 3rd Party App Analysis class and realized I never finished the work I started with Bumble on Android so here we are. I was actually able to make some small breakthroughs on new artifacts since I last look at it so let's see what we can find.
For test data, I used the CTF image from the Magnet Virtual Summit 2022. The main Bumble app folder lives at:
There were two main files of interest that I was able to find artifacts and we will look at those below.
Settings
The settings file is actually a little hidden or obfuscated. Found at the following path is the file we are looking for:
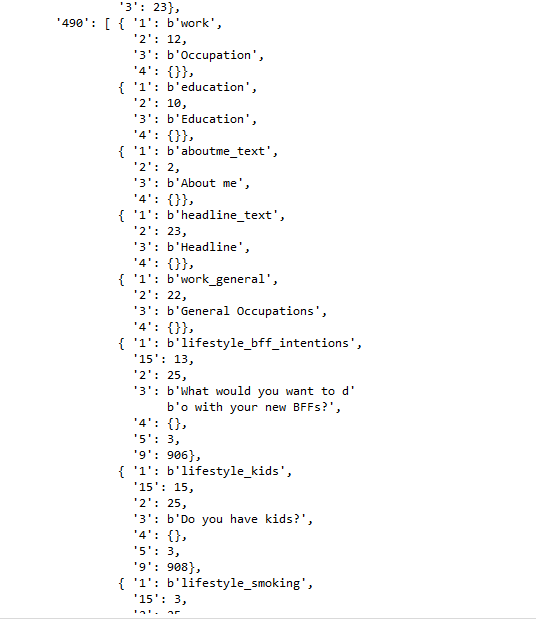
I quickly dropped into my Python IDE to start putting together a rough script utilizing Yogesh's blackboxprotobuf libary to make it a little more readable. There are over 500 lines that it traverses but only a handful are comprehendible without knowing further context of how the account was set up through the app. A few specifics I could pull were user name, email address, birthdate and age, user ID, some location details, a partially redacted phone number as well as some questionnaire personal details.
Chat Messages & Matches
The main file that contains chat and match connection details can be found at:
data\data\com.bumble.app\databases\ChatComDatabase*
Note: always make sure to get the -wal
It's a normal formatted SQLite database which we've come to know well in Android land. We can open it in DB Browser or any other trusty SQLite tool. The tables of interest from which I found good data are:
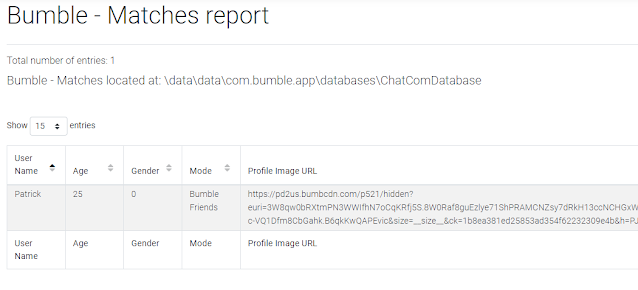
- conversation_info - contains matches and matched user details
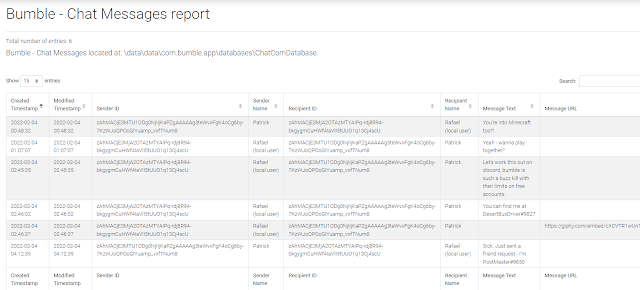
- message - contains all chat messages and further details
- user_name - name of the user that matched (first name)
- age - age set for the user that matched (this is user set so may not be accurate)
- gender - gender selected, more research needs to be done to determine what each may be (Bumble is very inclusive in their options)
- user_id - numerical ID of the user matched
- encrypted_user_id - same format of a user ID found in the user settings file
- game_mode - type of mode the user is using, 0 for Bumble Date, 1 for Bumble Friends, 5 for Bumble Bizz
- There may be more options but I'm not aware of them at time of publication
- user_image_url - URL path to the users avatar picture (may not be accessible publicly)
- created_timestamp - created date in Unix epoch millisecond format
- modified_timestamp - modified date in Unix epoch millisecond format (not sure if messages can be edited)
- sender_id - encrypted ID of the sender
- recipient_id - encrypted ID of the recipient
- payload - message or details being sent/received in embedded JSON
- payload_type - type of message being sent/received
- is_incoming - direction of the message, 0 for Outgoing, 1 for Incoming