Another beast has thawed from their ice slumber. Tusky is an alternative client app to the ever-growing and ever popular Mastodon. Similar to my breakdown for Mastodon I'll be going through what we can find in the folder structure via an Android phone dump.
The main folder we can find the app at is as follows:
data\data\com.keylesspalace.tusky
Like usual, the large chunk of the evidence will be in the SQLite database found at:
data\data\com.keylesspalace.tusky\databases\tuskyDB*
Make sure to get those -wal files per best practices. Taking a peak in the database file we get the following table structure:
Figure 1: tuskyDB table structure in DB Browser
Most tables were empty but I was able to find some useful stuff in the "AccountEntity" and "TimelineStatusEntity" tables.
AccountEntity - Account Details
The "AccountEntity" table had user account details and preferences. This included user, display and instance names, account ID's, avatar URLs, and a bunch of boolean switches that show if a user had notifications turned on for different interactions such as follow requests, boosts, favorites and more.
Other items include the tab preference layout on the phone, which gives a bit of a sense of how the user has it displayed. A quick and easy query shows results:
Figure 2: Account details in DB Browser
ALEAPP gives a similar simple look at this:
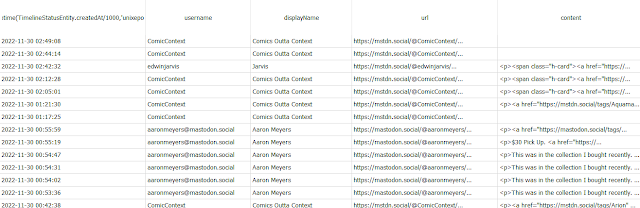
"TimelineStatusEntity" is similar to the "home_timeline" table from Mastodon. Here is where we get the content and statuses of what the user is seeing on their timeline. I did a join with the "TimelineAccountEntity" to bring in more details on the users (such as username and display name). Here's a rundown of columns I found with useful information:
- createdAt - timestamp in Unix epoch milliseconds of the toot
- url - link to the toot update
- content - HTML format content of the toot
- attachments - JSON blob that includes URL links to attachment images/videos
- reblogsCount/favourtiesCount/repliesCounts - metrics for the toots
- visibility - visibility of the toot
- 1 = Public
- 4 = Direct / DM
- application - details on the app used to generate the toot (ex. Mastodon for iOS)
Figure 4: Timeline details in DB Browser
With some small manipulation via Python coding, we get some slick looking results in ALEAPP:
Figure 5: Timeline details in ALEAPP
This is just a brief foray into my findings of Tusky for Android but overall, the results seem pretty similar to what were found via Mastodon. This makes sense because Mastodon is really just feeding it all. With that said, if the suspected user has both installed on the phone (like I do currently) it might be worth your time to examine both incase one of the other has cached details that the other does not.
Grab the latest version of ALEAPP now with the included parser!